You first need to define the business problem that your IoT deployment is intended to solve. Understand the type of data that will be collected, the devices that you will be using, and the outcomes that you want to achieve from this deployment.
Device connectivity
Plan how the devices will connect to the IoT platform, including through using protocols such as MQTT or HTTPS. Design the data processing pipeline alongside this, such as by using AWS IoT Core, AWS Lambda, Amazon Kinesis, and Amazon S3. This will be imperative, as you need to understand how you can best ingest the data in your use case.
Data analysis and storage
You then need to design your data analysis solution. Understand the volume, velocity, and variety of the data that will be generated to help you design a solution that can handle the amount and complexity of the data.
Security and compliance
You need to then define the security and compliance requirements, along with the appropriate controls. Does your data need to stay within the country’s borders? Do you need to restrict access to certain services? You may use different services in AWS to achieve your goals, including AWS IAM, AWS KMS, and Amazon VPC.
Testing solution
You then need to put in place and test the solution, setting up a maintenance plan that includes monitoring, updating, and continuously optimizing the deployment’s performance. It is from here that you will iteratively build on the setup of the infrastructure, as there will be a continuous need for improvement within the system.
Now, let’s look at the design of one such architecture.
A simple architecture
As can be seen in the following figure, this is the design of one such architecture based on AWS. What do you think its use case is?
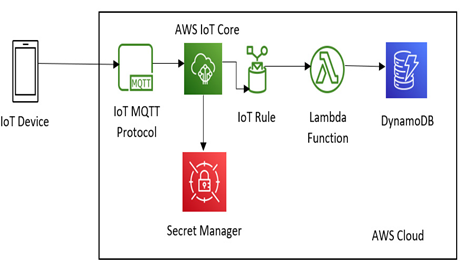
Figure 7.5 – A simple architecture that utilizes AWS IoT Core to serve an IoT device
We can see that we are obtaining data through the IoT device. We then transmit the data from the IoT device to AWS IoT Core through the IoT MQTT protocol. This is our first point of entry into the cloud. We then have AWS IoT Core reach into Secret Manager to get the appropriate authentication keys to decrypt the messages that are being transmitted. The AWS IoT Core will then read the IoT rule and act accordingly based on the filtered messages. It then sends the ones that match the rules through to the Lambda function, which will execute and store the data within DynamoDB.
Note that this solution has minimum security; most production-grade solutions have multiple layers of security. For example, they may have virtual private clouds (VPCs), which are customizable, isolated sections of the AWS cloud where users can launch and manage their own computing resources, or they may have a web application firewall to monitor incoming web traffic while sitting in front of the application.
Now we can look at evaluating our solution based on our deployment.
Leave a Reply