EC2 instances are web services that provide scalable compute capacity within the cloud, allowing users to launch virtual servers that can run a number of different operating systems and applications. These EC2 instances can be scaled up or down accordingly to meet the diversifying and changing computational needs that are part of users’ applications. Users are able to configure and customize their instances with an instance type, number of CPU cores, amount of memory, storage, and more. It also offers various security features, including the requirement to configure a key pair for accessing instances. Additionally, it provides a range of other security options suitable for both internal and client-facing applications. It is often the foundation of scalable, highly available, and fault-tolerant systems within the cloud.
AWS IoT Core
AWS IoT Core is a platform that facilitates the connection, management, and communication of IoT devices with AWS services alongside other devices that may be used within the network. It connects devices securely, allowing for storage and analyzing capabilities through other services. It provides several features, including MQTT and HTTP protocols, that can communicate with devices, register devices, provide device shadows, and understand how device data is processed. It can integrate with a number of other services, such as AWS Lambda, Amazon SNS, Amazon SQS, and more.
AWS IoT comprises the following components: the message broker, the rules engine, the Thing Registry, Thing Shadows, and the security and identity service. IoT devices can access the AWS cloud through multiple approaches, including via AWS IoT Core using the MQTT protocol, via AWS API Gateway using REST/HTTP or WebSocket, or via AWS LoRaWAN. The message broker offers a secure way for IoT devices to publish and receive messages from each other using either the MQTT protocol or the HTTP REST interface. The rules engine facilitates the processing of messages and assists in integrating the workload with other AWS services. The Thing Registry helps to organize resources linked to each thing, while Thing Shadows provide persistent representations of things within the AWS cloud. Additionally, the Security and Identity Service ensures security in the AWS cloud through shared responsibility, requiring IoT devices to maintain their credentials securely to send data safely to the message broker.
The following is a diagram depicting how AWS IoT works:
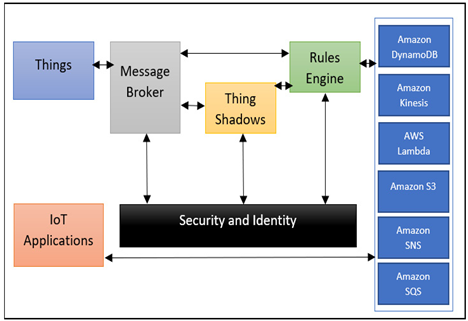
Figure 7.1 – How AWS IoT works
AWS IoT has Things within the network report their current state through JSON messages to MQTT topics. The message broker distributes incoming messages from a topic to all its subscribers. Rules can be established to determine actions based on the content of these messages. We can, for example, invoke a Lambda function or query a table within one of the storage solutions connected to our network. We can also filter the message, and when a rule matches the filtered message, it will perform the action that has been selected with the properties. The rules also have an IAM role that grants AWS IoT permission to access the AWS resources that were used to perform the action.
Each thing also has a Thing Shadow, which is able to store and retrieve the state information. Each piece of state data consists of two parts: the most recent status reported by the object and the state that an application wishes for it. An application can ask for the current status details of a specific object. In response, the shadow provides a JSON file that includes both the current and desired states, a version identifier, and additional details. Through this, an application can instruct an object to alter its state. The shadow can accept the request for the change within the state, update the state information, and send a message that shows that the information for the state has been updated. The thing then receives the message, accordingly makes the change to its state, and reports on its new state.
With that, we can look at AWS IoT Greengrass, an important complement to AWS IoT Core that we will be seeing used later in the chapter.
Leave a Reply